OculusIT understands the critical role cybersecurity plays in ensuring the success of your institution. In today’s ever-evolving threat landscape, a robust security posture is no longer optional – it’s essential. That’s where comprehensive CISO services come in. With comprehensive CISO services, your institution gains a proactive approach to cybersecurity, hence empowering your institution’s security posture.
Struggling to Keep Up with Cyber Threats?
Evolving threat landscape, limited resources, and budget constraints – sound familiar? These are just some of the cybersecurity challenges that many higher education institutions face today. Cybercriminals are constantly developing new methods to exploit vulnerabilities, while institutions often lack the in-house expertise and resources to effectively combat these threats.
If these challenges resonate with you, then it’s the right time to consider partnering with a CISO service provider.
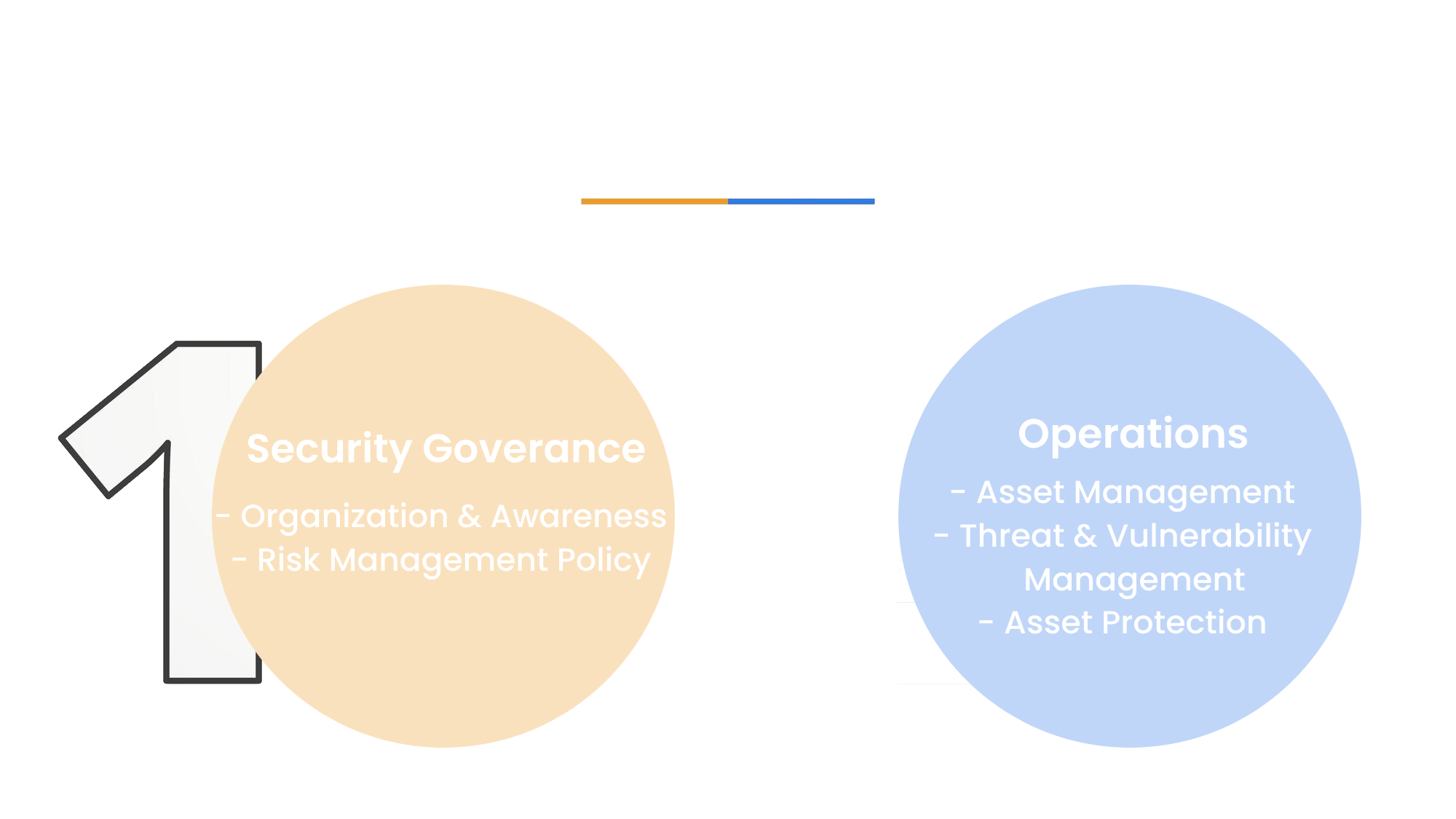
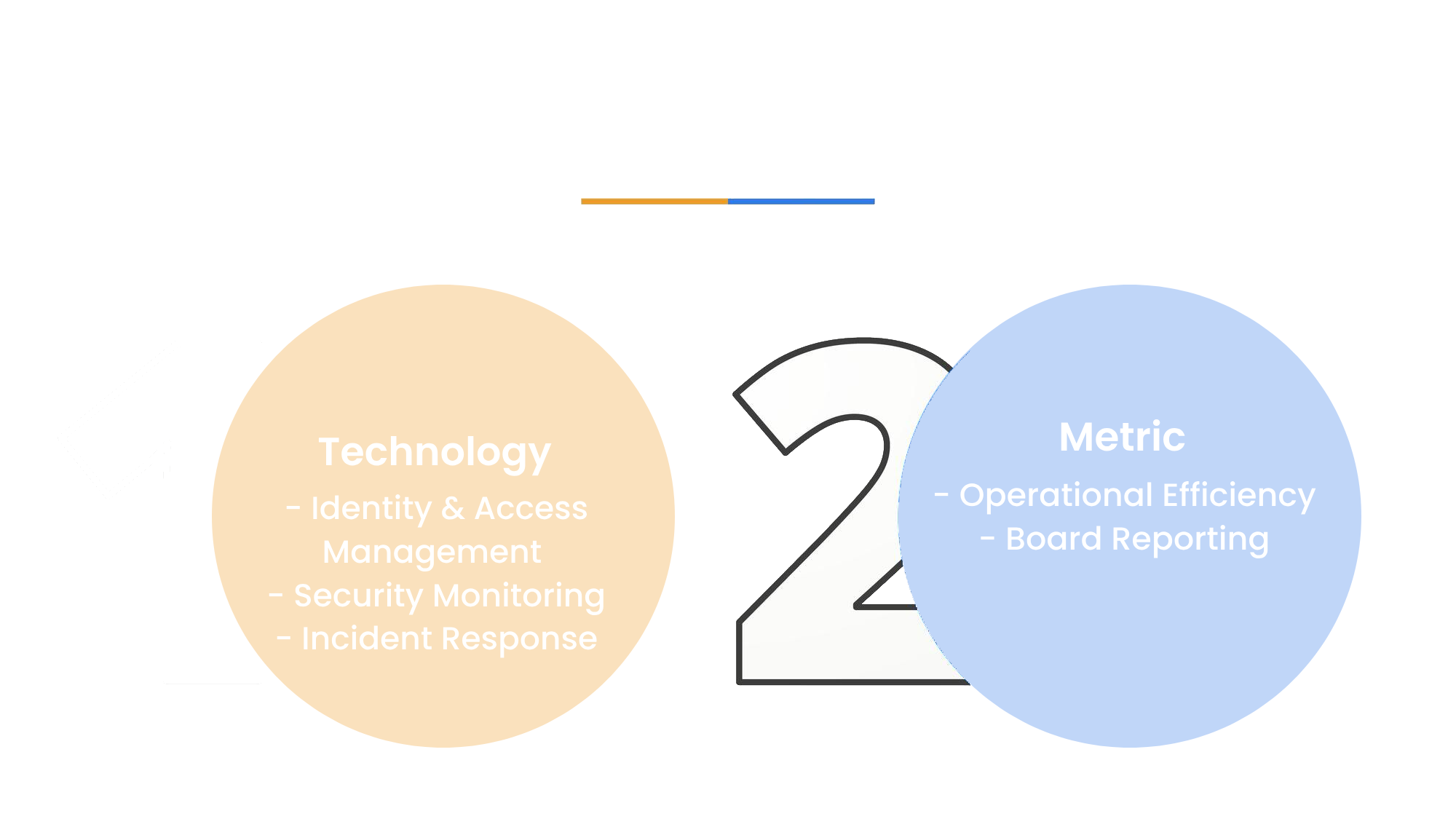
Benefits of CISO services
- Enhanced cyber threat protection
- Informed decision-making support
- Improved incident response coordination
- Comprehensive security posture assessments
- Industry Trend Updates for Preparedness
- Access to cybersecurity architecture expertise
- Regulatory compliance assistance
- Cybersecurity training and awareness programs
Services under Chief Information Security Officer Services
![]()
Strategic Security
![]()
Superior Advisory
![]()
Planning & Tracking
![]()
Policy Development
![]()
Senior Presentations
![]()
Unbiased Coordination
OculusIT’s Approach to A Completely Managed Solution
Let’s get in touch!
OculusIT is a global, all-inclusive, managed IT services company exclusively for higher education. Get a higher return on your IT investment now!





